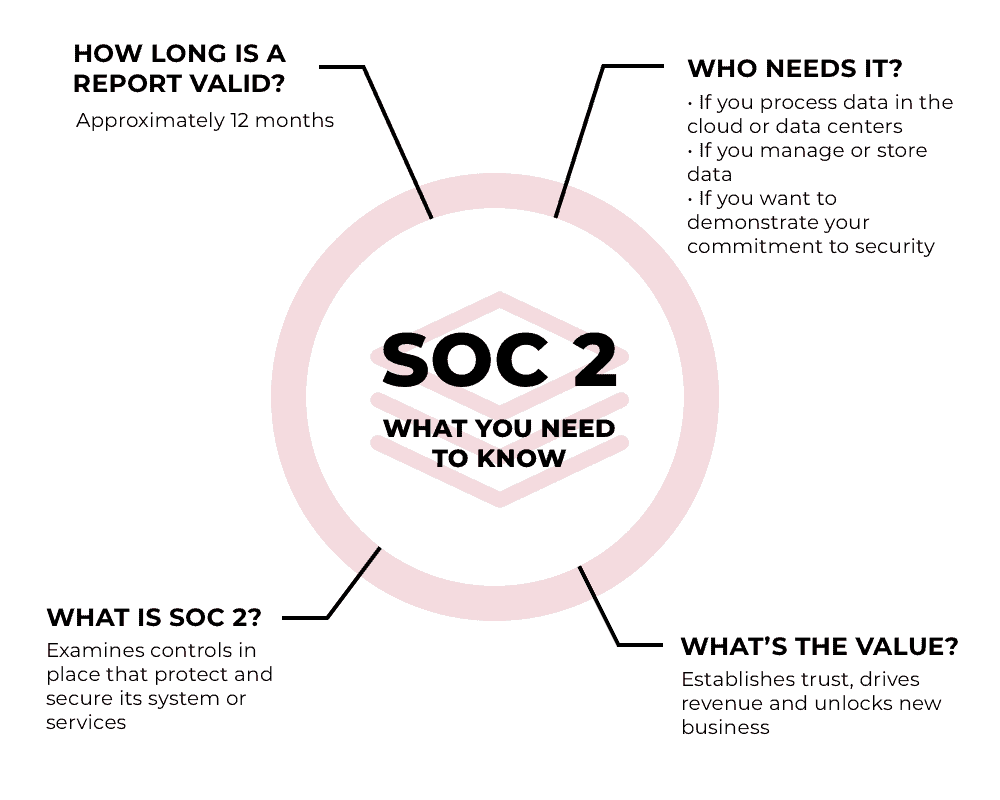
SOC 2
The SOC 2 audit is an extremely popular form of cybersecurity audit, used by a rapidly growing number of organizations to demonstrate they take cybersecurity and privacy seriously.
In a world filled with data breaches and information leaks, establishing trust is not only critical to your revenue stream, but it can be a competitive differentiator when closing new business. Customers and partners seek assurances that the companies they work with are doing everything they can to avoid exposing sensitive information and creating risk. That’s exactly what SOC 2 does.
WHAT IS SOC 2?
SOC, which stands for System and Organizational Controls, is a framework developed by the American Institute of Certified Public Accountants (AICPA) for the purpose of providing regular, independent attestation of the controls that a company has implemented to mitigate information-related risk.
There are actually three types of SOC audits: SOC 1, SOC 2, and SOC 3. When it comes to cybersecurity, SOC 2 has become the de facto standard.
In a SOC 2 audit, you describe the policies, procedures, and systems you have in place to protect information across five categories called Trust Services Criteria. Your independent auditor evaluates the evidence you supply for the controls in each category, and when completed you receive your official SOC 2 report that you can share with customers and business partners to assure them that their data will be handled securely.
Certified security professionals

We are compliant

The right weapons
PLEASE FILL OUT THE FORM BELOW
We don’t just help you become compliant. We help you take control of your security future.
