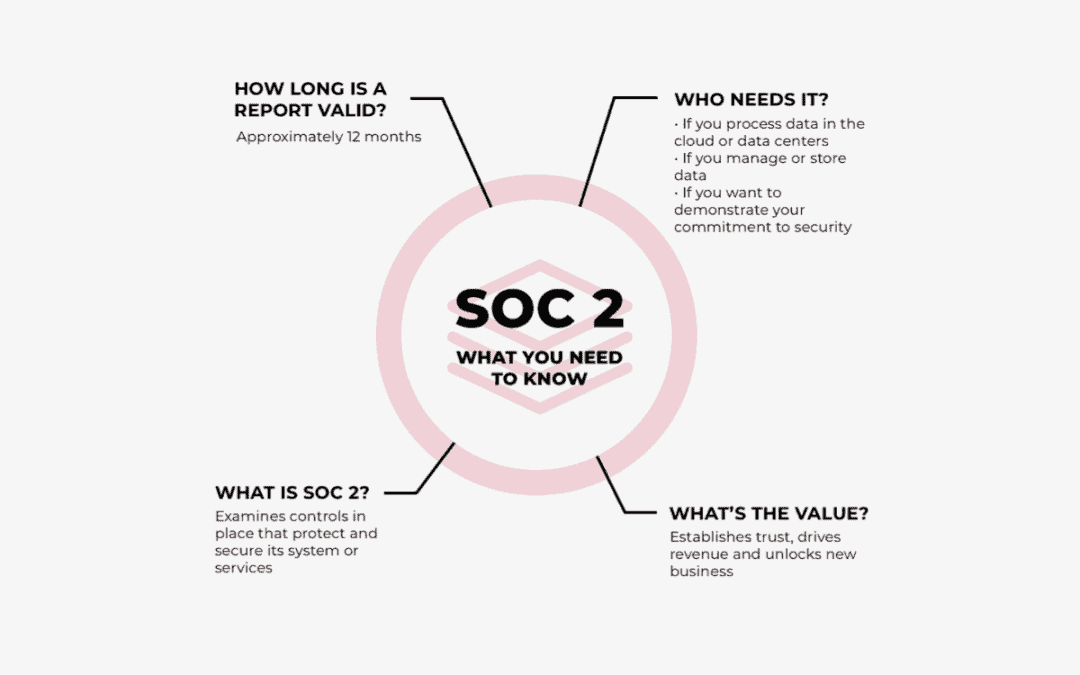
The Impact of AI on Phishing in IT Security
AI Phishing Attacks
In the ever-changing landscape of information technology (IT), artificial intelligence (AI) has emerged as a game-changer, transforming various aspects of cybersecurity.
One significant area where AI has both amplified and combated threats is phishing attacks. Let’s explore the effects of AI phishing attacks in the world of IT.
In this blog, you’ll learn about:
1. Sophistication of Phishing Attacks: AI has empowered cybercriminals to create highly sophisticated and personalized phishing campaigns. Attackers can analyze vast amounts of data to craft convincing messages that target specific individuals or organizations. This level of personalization significantly increases the success rate of phishing attempts.
2. Automated Phishing Campaigns: AI enables cybercriminals to automate phishing campaigns on a massive scale. With minimal effort, attackers can target many users simultaneously, increasing their chances of finding vulnerable targets. Automated phishing kits powered by AI have become readily available on the dark web, allowing even non-technical criminals to launch sophisticated attacks.
3. Early Detection and Prevention: On the flip side, AI is also playing a crucial role in detecting and preventing phishing attacks. By continuously learning from previous attacks, AI-driven systems can adapt and stay one step ahead of evolving phishing techniques.
4. Reduced False Positives: AI-driven anti-phishing solutions help reduce the false positives that traditional systems often generate. By accurately distinguishing between legitimate emails and phishing attempts, AI contributes to a more efficient and streamlined security process, enabling IT teams to focus on actual threats.
5. Enhanced Incident Response: If a phishing attack does succeed, AI can quickly identify affected systems, assess the damage, and aid in mitigating the consequences.
In conclusion, AI has introduced both challenges and opportunities in the fight against phishing attacks in the IT world. While cybercriminals leverage AI to create more sophisticated and widespread threats, security professionals are also leveraging AI’s capabilities to detect and prevent these attacks more effectively. To stay ahead in this relentless battle, organizations must embrace AI-driven cybersecurity solutions while ensuring continuous education and training to empower their workforce against evolving phishing tactics.