Outlining the CMMC Process: Gap Analysis and SPRS Score
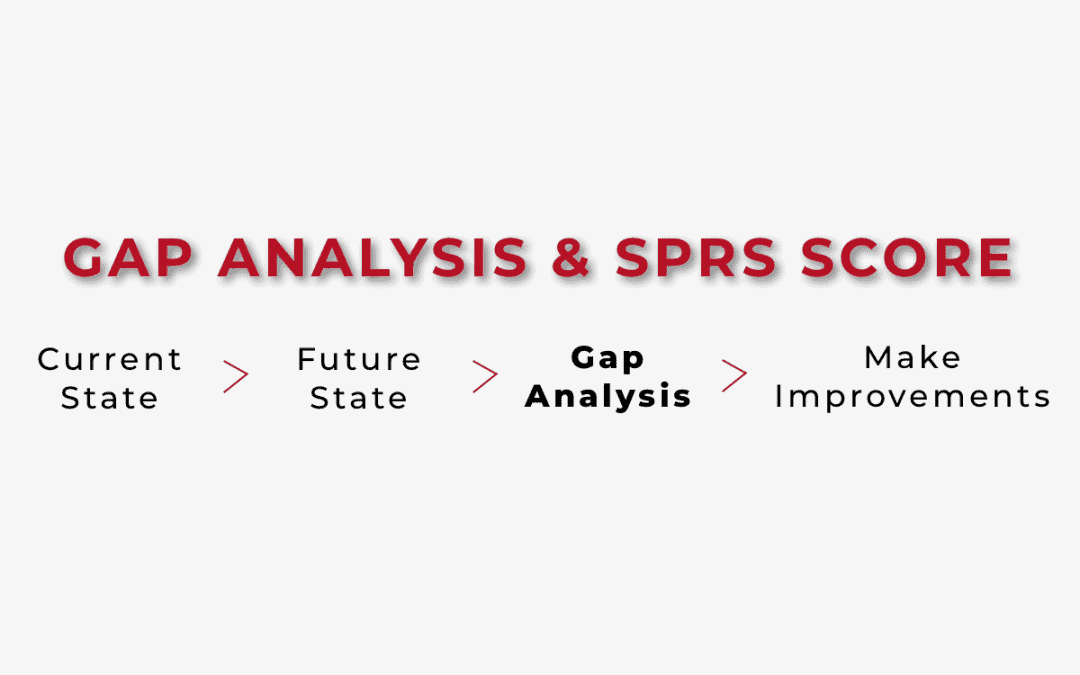
Perform a Gap Analysis
What’s a gap analysis and why is it necessary?
Great question…
A gap analysis is the process of identifying the gaps between your organization’s current cybersecurity practices and the practices required by the CMMC framework.
A gap analysis helps organizations identify the areas where they need to improve to meet the certification requirements.
Gap Analysis Process
The process involves reviewing your current policies, procedures, and controls to identify any areas that need to be updated or improved.
We take two to three (2 to 3) virtual or in-person meetings to determine where your company currently stands with CMMC requirements.
What’s the Result of a Gap Analysis?
The result of a gap analysis is a report that highlights the gaps between your current practices and the CMMC requirements. This report can be used to develop a plan to address the gaps and achieve compliance.
Our cyber security professionals review your assessment and provide recommendations through conversations with you about how to make CMMC work best for your company.
Deliverables involved:
- Gap Analysis
- SPRS Score
- A detailed quote for any requested IT or policy services
What’s a SPRS Score?
The SPRS score is a rating system used by the Department of Defense (DoD) to assess the cybersecurity practices of its suppliers.
The SPRS score is based on a cybersecurity assessment questionnaire that suppliers must complete.
The questionnaire evaluates the supplier’s compliance with the cybersecurity requirements outlined in the Defense Federal Acquisition Regulation Supplement (DFARS) and the NIST SP 800-171 cybersecurity framework.
The SPRS score ranges from 0 to 110, with a higher score indicating better compliance. A score of 110 is required for suppliers to be eligible to bid on certain contracts.
In the context of CMMC compliance, the SPRS score is used to assess a supplier’s readiness to achieve certification. The SPRS score can help organizations identify areas where they need to improve to meet the certification requirements. The score is used by the DoD to prioritize suppliers for assessment and to monitor the cybersecurity practices of its suppliers.
Why You Need Gap Analysis and SPRS Score for CMMC?
In summary, gap analysis and SPRS score are important tools for organizations seeking to achieve CMMC compliance. Gap analysis helps organizations identify the areas where they need to improve to meet the certification requirements, while SPRS score is used to assess a supplier’s readiness to achieve certification and to monitor the cybersecurity practices of its suppliers.