Here's Our Top 4 Tips...As remote work continues to become the norm, we're here to support your transition with essential tools and security measures. Check out our top for tips for working effectively from home. 1. Seamless Communication Phone Software: Answer and...
READ ON
Blog
We take pride in assisting our customers with IT solutions, deep-diving insight, and best practices to help move their business forward. We understand that you have to give to get, and, of course, our intention is to serve our customers as politely and respectfully as possible. All-in-all, we strive for mutually beneficial relationships.
Read our blog and see how we can benefit your business.
Quarterly Cyber Breach Updates: Protect Your Business Data
2023 Q39/6/2023 GVSU warns students of data breach that could protect personal dataYes, it's true... Cyber breaches can occur anywhere. This week, Grand Valley State University has issued a warning to certain students regarding a data breach involving their personal...
How to Enroll in MFA with Microsoft Authenticator App
Follow the steps below to activate Microsoft Multi-factor Authentication1. Sign into your work or school account and then go to My Account portal.2. Select Security info in the left menu or by using the link in the Security info pane. If you have already registered,...
The Impact of AI on Phishing in IT Security
AI Phishing AttacksIn the ever-changing landscape of information technology (IT), artificial intelligence (AI) has emerged as a game-changer, transforming various aspects of cybersecurity. One significant area where AI has both amplified and combated threats is...
Streamlining Your Communication Setup: Holiday Edition
Mastering Holiday Communication: Simple Steps for Seamless ConnectionsAs professional workers, maintaining effective communication during holiday weekends or holidays is crucial. To ensure a smooth workflow and uninterrupted communication, it's essential to set up...
Stay protected with Cyber Breach Warranty
Get Protected with up to $300,000We understand that cyber threats are a constant concern for businesses like yours. Our security stack has top-notch antivirus software and security measures. That's why ICS Data provides a $300,000 Cyber Breach Warranty to allow you...
Organizing Your Digital Files: 11 Helpful Tips
11 of our most helpful digital file organization tips:In today's world, we rely more and more on digital files for work and personal use. That's why it's important to have a system in place for managing them. A well-organized digital filing system can save you time,...
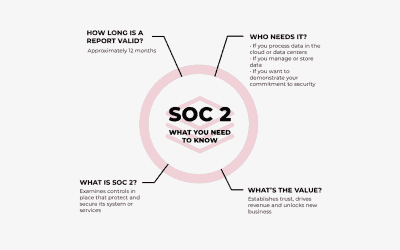
Why SOC 2 Compliance Matters for Data Security
Why is SOC 2 Compliance important?In today's digital age, the security of information has become increasingly important. Many companies rely on third-party service providers to handle sensitive information such as financial and personal data. These service providers...
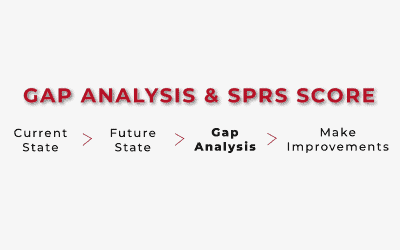
Outlining the CMMC Process: Gap Analysis and SPRS Score
Perform a Gap AnalysisWhat's a gap analysis and why is it necessary? Great question... A gap analysis is the process of identifying the gaps between your organization's current cybersecurity practices and the practices required by the CMMC framework. A gap analysis...